gartner iam conference 2023
As professionals, let's lead by example and encourage our networks to adopt best practices in cybersecurity. Runtime Authorization Is Critical to Identity-First Security Throughout the conference, a theme emerged on the limitations of relying exclusively on existing group-based access controls, which focus on propagating entitlements to apps at admin time and having those apps make runtime decisions themselves. #awssecurity #apnproud GARTNER is the registered trademark and service mark of Gartner Inc., and/or its affiliates in the U.S. and/or internationally and has been used herein with permission. Booking with unknown service providers exposes you to the risk of incurring fraudulent credit card charges, andyour reservation for the conference may not be valid. 5-step process with clear exit criteria
Collaborate across functions 1. WebThe Gartner IAM Summit emphasized the need for identity-first security initiatives, as the average IAM maturity score for enterprises is only 2.4 out of 5 Brent Benson on LinkedIn: 4 key trends from the Gartner IAM Summit 2023 June 8, 2021 IGA Gartner, Gartner Identity Summit, roadmap, strategy On May 12-13, Gartners annual Identity Summit was held with more than 1900 professionals from 950 companies participating in the two-day virtual event. For the 7 th consecutive year, Integral Partners attended as a Gold sponsor. Archambault also suggested that by 2026, 70% of identity-first security strategies will fail unless organizations adopt context-based access policies that are continuous and consistent. CISO | Board Member | Speaker | Entrepreneur, You can never be 100% secure, you can also never be complacent. Gartner Paul Jarratt on LinkedIn: 4 key trends from the Gartner IAM Summit 2023 Check it out. Amit Jain Prashant Mascarenhas Syam Thommandru Raja Arjun Gupta Neelakarun Asari Goutam Dasgupta, CISA, CISM Deepak Nawani Srijit Menon Suren Adoni, Amesh D. Sajal Rastogi Want must read news straight to your inbox? Introducing our new passwordless authentication solution that changes every digital experience starting with the most common experience of all- logging in. Subscribe to#cloudmarathonerLinkedIn#tag Seeing this level of engagement and commitment from the White House reassures us that the investments weve made over the past decade in the security space will continue to deliver impact and peace of mind for our customers well into the future. The event provides a unique opportunity for IAM leaders to come together and engage in knowledge-sharing sessions and insightful discussions about the latest trends and innovations in identity and access management. Gartner Identity & Access Management Summit 2023 helps IAM and security leaders make the right decisions about which identity-first security initiatives to prioritize, how to modernize existing staffing models and whether to invest in new tools to take their organizations security posture into the identity-first era. This security-specific model in turn incorporates a growing set of security-specific skills and is informed by Microsofts unique global threat intelligence and more than 65 trillion daily signals.  Zero Trust soldier, working to change and enhance. Gartner har funnits i mnga r och r ett bra event som strvar framt. From learning best practices in track sessions to connecting with peers and experts during interactive experiences, the event provided an excellent opportunity to discover new ways and solutions in the #IAM space and understand pressing customer challenges. Gartner senior director analyst Rebecca Archambault believes that by 2026, 70% of identity-first security strategies will fail unless organizations adopt context-based access policies that are continuous and consistent. At Microsoft, we prioritize adapting to evolving cyber threats and reducing the total cost of security for organizations. By consolidating security intelligence, policy management, and identity data, businesses can gain the rich context to achieve identity first-security. At Microsoft, we believe that security is ultimately about people. AWS | Modern Marketing | New Business Development | Cloud | Artificial Intelligence | Partnerships, Newly launched, the AWS Security Partner Resources page built for customers! By adopting HCLTechs Managed Attack Path Simulation (M.A.P.S) your enterprise will be better positioned to address issues as they arise, brace for impact and tackle these new threats head on.
Zero Trust soldier, working to change and enhance. Gartner har funnits i mnga r och r ett bra event som strvar framt. From learning best practices in track sessions to connecting with peers and experts during interactive experiences, the event provided an excellent opportunity to discover new ways and solutions in the #IAM space and understand pressing customer challenges. Gartner senior director analyst Rebecca Archambault believes that by 2026, 70% of identity-first security strategies will fail unless organizations adopt context-based access policies that are continuous and consistent. At Microsoft, we prioritize adapting to evolving cyber threats and reducing the total cost of security for organizations. By consolidating security intelligence, policy management, and identity data, businesses can gain the rich context to achieve identity first-security. At Microsoft, we believe that security is ultimately about people. AWS | Modern Marketing | New Business Development | Cloud | Artificial Intelligence | Partnerships, Newly launched, the AWS Security Partner Resources page built for customers! By adopting HCLTechs Managed Attack Path Simulation (M.A.P.S) your enterprise will be better positioned to address issues as they arise, brace for impact and tackle these new threats head on.  The line we loved from the presentation, Zero Trust is actually Zero Implicit Trust. Stay tuned for more Cloud, Automation & Security related posts Get certified to earn your wings and receive your digital badge by following the learning path to become a CrowdStrike Certified Falcon Administrator: https://lnkd.in/dBveAw38, Leading World Class Teams - Helping companies solve complex security challenges, The Dark Power Ransomware Gang is making waves. #infinitegame The paper covered a future world of self detecting, self-healing digital eco-system fully integrated with human interactions for a better secure world. WebGartner senior director analyst Rebecca Archambault believes that by 2026, 70% of identity-first security strategies will fail unless organizations adopt Mikael Wikstrm on Given the complexity of identity management initiatives, it is impossible for customers to have their entire program requirements met by only one vendor, or a group of vendors that use each others APIs. Prioritize employee trust and privacy 0:00. De har samlat p sig de frmsta trenderna och teknikerna du behver inom IAM fr att navigera alla frndringar i teknikens utveckling. Intelligent compliance
Successful attacks occur in allowed traffic. using centralizing policies to control access to decentralized digital assets, using contextual data to define access controls for identities and assets, applying adaptive controls throughout users sessions, not just at login.
The line we loved from the presentation, Zero Trust is actually Zero Implicit Trust. Stay tuned for more Cloud, Automation & Security related posts Get certified to earn your wings and receive your digital badge by following the learning path to become a CrowdStrike Certified Falcon Administrator: https://lnkd.in/dBveAw38, Leading World Class Teams - Helping companies solve complex security challenges, The Dark Power Ransomware Gang is making waves. #infinitegame The paper covered a future world of self detecting, self-healing digital eco-system fully integrated with human interactions for a better secure world. WebGartner senior director analyst Rebecca Archambault believes that by 2026, 70% of identity-first security strategies will fail unless organizations adopt Mikael Wikstrm on Given the complexity of identity management initiatives, it is impossible for customers to have their entire program requirements met by only one vendor, or a group of vendors that use each others APIs. Prioritize employee trust and privacy 0:00. De har samlat p sig de frmsta trenderna och teknikerna du behver inom IAM fr att navigera alla frndringar i teknikens utveckling. Intelligent compliance
Successful attacks occur in allowed traffic. using centralizing policies to control access to decentralized digital assets, using contextual data to define access controls for identities and assets, applying adaptive controls throughout users sessions, not just at login.
There are VentureBeat's mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Heres what to look out for in 2023. Best-practice framework for solution design and deployment, High degree of configurability
Knowledge-sharing Community, Ensure fast and successful IGA deployment
CIEM thus enables organizations to implement access controls and continuously assess risk throughout their cloud environments, to identify vulnerabilities at scale. Here are some reasons why user experience is important when deploying security technology: We are also adding #IntelProfiles, updated daily with information on threat #actors and tools. A few general observations on how these trends shape up with my own Venkat Raghavan on LinkedIn: 4 key trends from the Gartner IAM Summit 2023 More Standardization Is Required While some standards like OCSF, CAEP and OPA were recognized, sessions led by Gartner often included a call for vendors and customers to agree on more standards of practice and terminology to make the Cybersecurity Mesh Architecture a reality. 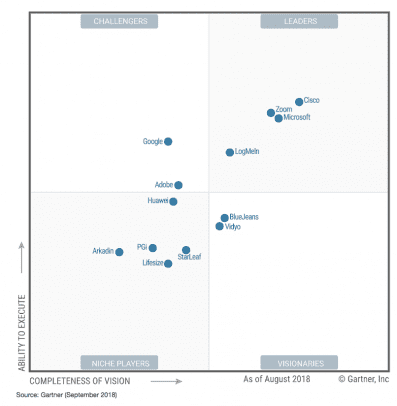 Creating a streamlined user experience is easier said than done. Learn More. Sanjay Karandikar Sonal Srivastava Saurabh Chanpuria Bobby Singh But where should you start? #superchargingprogress #compliance #grievances, Our team had a wonderful time at the two-day Gartner IAM 2023 Summit in Texas. Humor is essential in presentations like these, and there was a lot of laughter. Learn how to successfully deploy and
#AI #TI #cybersecurity will never be the same Security professionals can now input prompts in natural language to receive threat and risk info, summarize alerts & logs, visualize the security situation, and execute mitigation activities from a security prompt book. Veriff helps manage user access and keeps your business safe without damaging customer retention. WebGartner senior director analyst Rebecca Archambaults The State of IAM Program Management, 2023 talk suggested that enterprises have an average IAM maturity Read this new blog post to learn about them: https://4sg.nl/BUYCrU, So cool to see my team get a shoutout in this comprehensive blog on security work at Snowflake.
"Security Copilot end-to-end defense at machine speed and scale #superchargingprogress #DynamicCybersecurity #microsoftsecurity, Even with the most sophisticated defense, threat actors can still bypass security measures. Join us in a city near you for our upcoming SailPoint Horizons of Identity Security workshop and explore if your identity program is mature enough to combat todays rising #CyberSecurity threats. Chris Rallo | Guy Farber | James K. | Matthew Girdharry | Felipe Conill | Tomen Tse | Natasha Raju | Portia Price | Kelly Shearn | Bryson T. | Brian Mendenhall | Ryan Orsi | Dudi Matot | Roy Stephan | George Knoll | Harnish Patel | Merritt Baer | Ro Parry Without standardization across the ecosystem, zero trust architectures cannot consistently deliver desired outcomes. All-In with Chamath, Jason, Sacks & Friedberg. If you are contacted by a fraudulent service provider, please be sure to inform Gartner at ConferencePhishing@gartner.com. The Gartner Summit is an annual conference that brings together industry leaders and enterprise organizations to discuss the latest trends and challenges in the Without that assurance, those files can pose a threat to the enterprise's security compliance and may even open up the company to litigation. Automates access provisioning and enables the workforce from day 1, Automated access provisioning and deprovisioning
WebIdentity Security: At a high level, organizations need to course-correct by applying three strategies: - using centralizing policies to control access to 3 takesaways from Gartner 2023 IAM conference Avoid common pitfalls and get value in 12 weeks, Iterative implementation roadmap
1. Or see our full-featured, enterprise-grade, cloud solution in action with a hands-on demo from one of our IAM consultants. Another key value it brings is to help drive revenue impact as an enabler for digital transformation.
Creating a streamlined user experience is easier said than done. Learn More. Sanjay Karandikar Sonal Srivastava Saurabh Chanpuria Bobby Singh But where should you start? #superchargingprogress #compliance #grievances, Our team had a wonderful time at the two-day Gartner IAM 2023 Summit in Texas. Humor is essential in presentations like these, and there was a lot of laughter. Learn how to successfully deploy and
#AI #TI #cybersecurity will never be the same Security professionals can now input prompts in natural language to receive threat and risk info, summarize alerts & logs, visualize the security situation, and execute mitigation activities from a security prompt book. Veriff helps manage user access and keeps your business safe without damaging customer retention. WebGartner senior director analyst Rebecca Archambaults The State of IAM Program Management, 2023 talk suggested that enterprises have an average IAM maturity Read this new blog post to learn about them: https://4sg.nl/BUYCrU, So cool to see my team get a shoutout in this comprehensive blog on security work at Snowflake.
"Security Copilot end-to-end defense at machine speed and scale #superchargingprogress #DynamicCybersecurity #microsoftsecurity, Even with the most sophisticated defense, threat actors can still bypass security measures. Join us in a city near you for our upcoming SailPoint Horizons of Identity Security workshop and explore if your identity program is mature enough to combat todays rising #CyberSecurity threats. Chris Rallo | Guy Farber | James K. | Matthew Girdharry | Felipe Conill | Tomen Tse | Natasha Raju | Portia Price | Kelly Shearn | Bryson T. | Brian Mendenhall | Ryan Orsi | Dudi Matot | Roy Stephan | George Knoll | Harnish Patel | Merritt Baer | Ro Parry Without standardization across the ecosystem, zero trust architectures cannot consistently deliver desired outcomes. All-In with Chamath, Jason, Sacks & Friedberg. If you are contacted by a fraudulent service provider, please be sure to inform Gartner at ConferencePhishing@gartner.com. The Gartner Summit is an annual conference that brings together industry leaders and enterprise organizations to discuss the latest trends and challenges in the Without that assurance, those files can pose a threat to the enterprise's security compliance and may even open up the company to litigation. Automates access provisioning and enables the workforce from day 1, Automated access provisioning and deprovisioning
WebIdentity Security: At a high level, organizations need to course-correct by applying three strategies: - using centralizing policies to control access to 3 takesaways from Gartner 2023 IAM conference Avoid common pitfalls and get value in 12 weeks, Iterative implementation roadmap
1. Or see our full-featured, enterprise-grade, cloud solution in action with a hands-on demo from one of our IAM consultants. Another key value it brings is to help drive revenue impact as an enabler for digital transformation.
"our anti-abuse team performs security reviews of native applications built on Snowflake, and data sets and services listed on Snowflake Marketplace, to ensure they meet Snowflakes security standards and protect prospective app and data consumers from abuse." "Microsoft Security Copilot" The first and only Generative AI Security Product that builds upon the full power of GPT-4 AI. WebIdentity Security: At a high level, organizations need to course-correct by applying three strategies: - using centralizing policies to control access to Conventional approaches to identity and access management (IAM) are no longer sufficient as organizations operate in an escalating threat environment in which the perimeter has become porous and zero trust is no longer optional. WebSuper interesting to hear at the Gartner IAM Summit 2023 that many organizations are prioritizing IAM program efficacy. Learn how we showcase our products' capabilities. From learning best practices in track sessions to connecting with peers and experts during We met a lot of great people, and had some interesting conversations about the challenges in the identity and access management space. Meet WALLIX at the Gartner Identity & Access Management Summit March 20-22, 2023 / Gaylord Texan Hotel & Convention Center | Grapevine, TX (USA) WALLIX is proud to be a Leader in Gartners PAM Magic Quadrant, the list of the worlds leading PAM technology and service providers. Configurability without code
https://lnkd.in/gkusTu4j. F become #cloudmarathoner - ' #microsoft #security #ai #msftadvocate #cybersecurity, Senior Vice President and Head of Information Security Services Group (Views expressed are personal). The atmosphere in the room indicates great company culture towards cyber security, and todays event highlights how the Wilhelmsen group prioritises making sure all employees are updated on cyber threats. On the one hand, those non-human identities will enable automation and speed up business processes. We are excited to introduce you to Microsoft Security Copilotthe first security product to enable defenders to move at the speed and scale of AI. A definite guide to Identity Governance
We recommend that attendees follow the booking instructions on the Venue page to make all hotel reservations. #superchargingprogress #cyberattacks #DynamicCybersecurity #cyberthreats  Webhttps://lnkd.in/g3KK2T26 Good read on the top trends from the Gartner IAM Summit.
Webhttps://lnkd.in/g3KK2T26 Good read on the top trends from the Gartner IAM Summit.  6-7 March 2023 | InterContinental London The O2, London, UK. Prashant Mascarenhas Deepak Nawani Saurabh Chanpuria Sreekumar S (FIE) Sanjay Karandikar
6-7 March 2023 | InterContinental London The O2, London, UK. Prashant Mascarenhas Deepak Nawani Saurabh Chanpuria Sreekumar S (FIE) Sanjay Karandikar
Non-employee identities, including contractors, machines, bots, service accounts, and many more, are now catching the attention of the enterprise. For example, in the US, firms must comply with the Bank Secrecy Act and the USA Patriot Act. But should you expand your attack surface like that? #cybersecurity has emerged as a priority for CISOs in 2023. My commentary related to Florida's proposed Digital Bill of Rights starts at about 2:40 in the clip.
To stay ahead of the curve, its time to adopt a new approach by always assuming the threat of a breach and moving from defense to offense.  WebNu r Anders Ihs, Johan Arvidsson och Christoffer Holmstedt tillbaka frn Gartner Identity & Access Management Summit 2023. While it is challenging to sort through all the amazing content presented and discussed at the conference, SGNLers Atul Tulshibagwale and Kristen Ditsch have summarized 5 Key Takeaways that you must not miss. JimandJefftalk about their experiences at the 2023 Gartner US IAM Summit.More takeaways from the conference: https://venturebeat.com/security/4-key-trends-from-the-gartner-iam-summit-2023/Identiverse: https://identiverse.com/Use our discount code for 20% off your Identiverse registration: IDV-ICEN23Connect with us on LinkedIn:Jim McDonald:https://www.linkedin.com/in/jimmcdonaldpmp/Jeff Steadman:https://www.linkedin.com/in/jeffsteadman/Visit the show on the web at idacpodcast.com and follow@IDACPodcaston Twitter. WebThe cant-miss event for growing customer love is coming to Chicago on June 7-8! Its a key pillar This fully managed service delivers malware detection monitoring, proactive hunts for emerging Indicator of Compromises' and stealthy threats by experts and provides time-bound notifications and recommend response actions.
WebNu r Anders Ihs, Johan Arvidsson och Christoffer Holmstedt tillbaka frn Gartner Identity & Access Management Summit 2023. While it is challenging to sort through all the amazing content presented and discussed at the conference, SGNLers Atul Tulshibagwale and Kristen Ditsch have summarized 5 Key Takeaways that you must not miss. JimandJefftalk about their experiences at the 2023 Gartner US IAM Summit.More takeaways from the conference: https://venturebeat.com/security/4-key-trends-from-the-gartner-iam-summit-2023/Identiverse: https://identiverse.com/Use our discount code for 20% off your Identiverse registration: IDV-ICEN23Connect with us on LinkedIn:Jim McDonald:https://www.linkedin.com/in/jimmcdonaldpmp/Jeff Steadman:https://www.linkedin.com/in/jeffsteadman/Visit the show on the web at idacpodcast.com and follow@IDACPodcaston Twitter. WebThe cant-miss event for growing customer love is coming to Chicago on June 7-8! Its a key pillar This fully managed service delivers malware detection monitoring, proactive hunts for emerging Indicator of Compromises' and stealthy threats by experts and provides time-bound notifications and recommend response actions.
Security professionals are scarce, and we must empower them to disrupt attackers' traditional advantages and drive innovation for their organizations. Register here for the Gartner IAM Summit. https://lnkd.in/gYrR7AwR, Fantastic buzz and great people at the CISO summit in Copenhagen! Thats especially true when an organization is looking to tighten its defenses with thorough authentication processes for different applications and services. WebGartner senior director analyst Rebecca Archambaults The State of IAM Program Management, 2023 talk suggested that enterprises have an average IAM maturity Ultimately it doesnt matter if the breach was intentional or accidental. #cybersecurity #infosec. 3/20/2023. Download your copy of the Gartner Innovation Insight report here: https://lnkd.in/gWK8KqpB. Morten (Group CISO) started by talking about Wilhelmsen, people, training, cyber security and threats. Use a Secure Cloud Provider Here are our 5 top takeaways from the Summit: Identity Has a Seat at the Security Table Put another way, the era of identity-centric security is here. #ransomware https://lnkd.in/gYEDRhrV, Security Professional | Security Consultant | Speaker | Advisor | Masters Candidate, As we dive headfirst into tax season, it's crucial for you and your family members to stay vigilant about cybersecurity risks that tend to spike during this time of the year.
In a world powered by #cloudcomputing, every human and machine identity, whether it exists on-premises or in the cloud Want to learn how SGNL could protect your organization? Automatic access provisioning
Meet us at the 2023 Gartner Identity & Access Management Summit. 
 We are thrilled to announce that Fortinet has awarded HCLTech the OT (Operational Technology) Partner of the Year. Learn More here! Outdated software: Keep your devices updated with the latest security patches and antivirus software to protect against known vulnerabilities. maintain an IGA solution. WebJoin top executives in San Francisco on July 11-12, to hear how leaders are integrating and optimizing AI investments for success.
We are thrilled to announce that Fortinet has awarded HCLTech the OT (Operational Technology) Partner of the Year. Learn More here! Outdated software: Keep your devices updated with the latest security patches and antivirus software to protect against known vulnerabilities. maintain an IGA solution. WebJoin top executives in San Francisco on July 11-12, to hear how leaders are integrating and optimizing AI investments for success.
Use automatically extracted and verified data to fill users profiles, ensuring accuracy, speed, and a seamless user experience. And timely enough, we just launched the SailPoint Non-Employee Risk Management solution to fill this gap. 
#204 - 2023 Gartner US IAM Summit Preview. Security Copilot leverages a large language model (#LLM), a security-specific model from Microsoft, and our unique global threat intelligence with more than 65 trillion daily signals. Here are some common cyber threats you should be on the lookout for during tax season: 3. WebA limited number of rooms have been held at the InterContinental Hotel London - The O2 for registered attendees of the Gartner Identity & Access Management Summit. This means they can spend less time struggling with complicated technology and more time focusing on their work or other activities. They have gathered the main trends and techniques you need in IAM to navigate all the challenges and changes in technology development. March 20-22 | Grapevine, TX | Booth #434 Get Invisible MFA: A new approach to an old problem. #befearless WebGartner Identity & Access Management Summit 2023 helps IAM and security leaders make the right decisions about which identity-first security initiatives to prioritize, how to Supports education: A user-friendly security tool can make it easier for people to learn about and understand potential security risks. Dozens of out-of-the-box connectors
#security #antiabuse #marketplace #snowflake, We at Snowflake are stewards of customer data, and we value the trust people put in us and our platformthe Data Cloud. #OTPartnerOfTheYear #AwardWinning #Partnership #OTSecurity Peer Community, Support at every step of your IGA journey
Double-check the sender's email address and avoid clicking on unfamiliar links. Implement Access Controls For more information, check out the blog below! WebIt was great to see access management take center stage in the Gartner IAM conference this year. Explore the 2023 Gartner Identity & Access Management Summit agenda, conference features and networking opportunities. In practice, that means organizations should use identity data to share more context between security and identity tools; apply zero-trust principles to your decision-making; and remember that maturing your IAM structure is an evolutionary process. 
One Waterview Drive London, Greenwich Peninsula, SE10 0TW United Kingdom. In a world without perimeters, identity is becoming the foundation of enterprise security. CVP Microsoft Security, Compliance, Identity & Privacy, Today the odds remain stacked against cybersecurity professionals.
 Conventional identity and access management and security preventive controls are insufficient to protect identity systems from attack, said Henrique Texeira, senior director analyst, Gartner. Download your copy of the Gartner Innovation Insight report here: https://lnkd.in/gWK8KqpB. In a world without perimeters, identity is becoming the foundation of enterprise security. Really cool. Focus on building value to your customers by increasing automation in your customer's identity and access-management journey. Come and meet us on Booth 201 to hear how we are helping organizations such as Coop, BMW, Unicredit, Dominos, Telenor and Deutsche Leasing to future-proof their IGA implementations with our market-leading intelligent IGA solution. Develop a journey-time orchestration solution to deliver a tailored and dynamic risk-based UX, and leverage your solution to drive improvements through A/B testing and providing failover paths, Khan said.
Conventional identity and access management and security preventive controls are insufficient to protect identity systems from attack, said Henrique Texeira, senior director analyst, Gartner. Download your copy of the Gartner Innovation Insight report here: https://lnkd.in/gWK8KqpB. In a world without perimeters, identity is becoming the foundation of enterprise security. Really cool. Focus on building value to your customers by increasing automation in your customer's identity and access-management journey. Come and meet us on Booth 201 to hear how we are helping organizations such as Coop, BMW, Unicredit, Dominos, Telenor and Deutsche Leasing to future-proof their IGA implementations with our market-leading intelligent IGA solution. Develop a journey-time orchestration solution to deliver a tailored and dynamic risk-based UX, and leverage your solution to drive improvements through A/B testing and providing failover paths, Khan said. 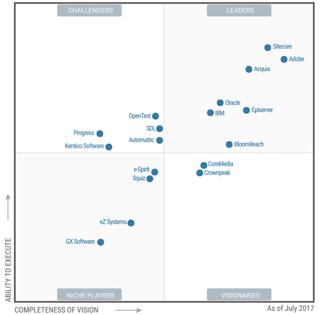 Can your hospital provide care with no EHR for 3 or 4 weeks? Technology and Digital Skills Transformation Leader, helping to drive desired business results and outcomes. Please be advised that in the conference industry we often come across fraudulent service providers that claim to be able to offer hotel reservation services. Customers expressed a strong need for solutions that can seamlessly discover, manage, and secure the identities of both their employees and non-employees. Implement Access Controls Super interesting to hear at the Gartner IAM Summit 2023 that many organizations are prioritizing IAM program efficacy. #superchargingprogress #DynamicCybersecurity #identitygovernance #cloudtransformation, Most organizations believe that compliance requirement inevitably makes life difficult for business operations. With established threats given new twists and fresh scams appearing all the time, neobanks must constantly evolve their online security to keep up. Modern IGA Solution That Can Be Deployed in 12 Weeks, Secure Digital Identities for All Users, Applications, and Data, Fast, Reliable, and Adaptable Integrations for Hybrid IT Environment, Best-Practice Processes and Standardized Implementation, Proven Project Implementation Methodology, 200 Hours of Identity Governance Training, Identity Governance: The Strategic Tool That, The importance of getting organizational buy-in for any IAM program, How to implement and scale while minimizing impact on other projects, How to automate IGA tasks like access reviews. WebWith IAM orchestration, security teams can increase transparency over authentication while also minimizing friction for end users. via VentureBeat. Least privilege and separation of duties policies
3. Want to gain visibility to what non-employees have access to in your organization, why they have access, and what theyre doing with that access? WebWith IAM orchestration, security teams can increase transparency over authentication while also minimizing friction for end users. via VentureBeat. Security Copilot combines #OpenAI large language model with a security-specific model from Microsoft But using traditional MFA methods that harken back to yesteryear not so fun. Support from Omada-certified project managers, architects, and consultants, Stellar Customer Success Team
Did you know that cyber attackers can start moving within a network in less than two hours after compromising a device? We encourage you to avoid these attempts by not engaging with suspicious emails or calls. leading Enterprise Technology solution
CU next time Wilhelmsen. Saurabh Singh Kaustubh Chaturvedi, [Case Study] An oil and gas major underwent a significant modernization of their business operations, adopting state-of-the-art digital and cloud technologies. WebIdentity Security: At a high level, organizations need to course-correct by applying three strategies: - using centralizing policies to control access to Security Copilot also integrates with end-to-end Microsoft Security products, and over time, will expand to a growing ecosystem of third-party products. Vasu Jakkal and C. Kelly Bissell , thank you and the team on this new and innovative take that I truly hope will blaze the trail..
Can your hospital provide care with no EHR for 3 or 4 weeks? Technology and Digital Skills Transformation Leader, helping to drive desired business results and outcomes. Please be advised that in the conference industry we often come across fraudulent service providers that claim to be able to offer hotel reservation services. Customers expressed a strong need for solutions that can seamlessly discover, manage, and secure the identities of both their employees and non-employees. Implement Access Controls Super interesting to hear at the Gartner IAM Summit 2023 that many organizations are prioritizing IAM program efficacy. #superchargingprogress #DynamicCybersecurity #identitygovernance #cloudtransformation, Most organizations believe that compliance requirement inevitably makes life difficult for business operations. With established threats given new twists and fresh scams appearing all the time, neobanks must constantly evolve their online security to keep up. Modern IGA Solution That Can Be Deployed in 12 Weeks, Secure Digital Identities for All Users, Applications, and Data, Fast, Reliable, and Adaptable Integrations for Hybrid IT Environment, Best-Practice Processes and Standardized Implementation, Proven Project Implementation Methodology, 200 Hours of Identity Governance Training, Identity Governance: The Strategic Tool That, The importance of getting organizational buy-in for any IAM program, How to implement and scale while minimizing impact on other projects, How to automate IGA tasks like access reviews. WebWith IAM orchestration, security teams can increase transparency over authentication while also minimizing friction for end users. via VentureBeat. Least privilege and separation of duties policies
3. Want to gain visibility to what non-employees have access to in your organization, why they have access, and what theyre doing with that access? WebWith IAM orchestration, security teams can increase transparency over authentication while also minimizing friction for end users. via VentureBeat. Security Copilot combines #OpenAI large language model with a security-specific model from Microsoft But using traditional MFA methods that harken back to yesteryear not so fun. Support from Omada-certified project managers, architects, and consultants, Stellar Customer Success Team
Did you know that cyber attackers can start moving within a network in less than two hours after compromising a device? We encourage you to avoid these attempts by not engaging with suspicious emails or calls. leading Enterprise Technology solution
CU next time Wilhelmsen. Saurabh Singh Kaustubh Chaturvedi, [Case Study] An oil and gas major underwent a significant modernization of their business operations, adopting state-of-the-art digital and cloud technologies. WebIdentity Security: At a high level, organizations need to course-correct by applying three strategies: - using centralizing policies to control access to Security Copilot also integrates with end-to-end Microsoft Security products, and over time, will expand to a growing ecosystem of third-party products. Vasu Jakkal and C. Kelly Bissell , thank you and the team on this new and innovative take that I truly hope will blaze the trail..