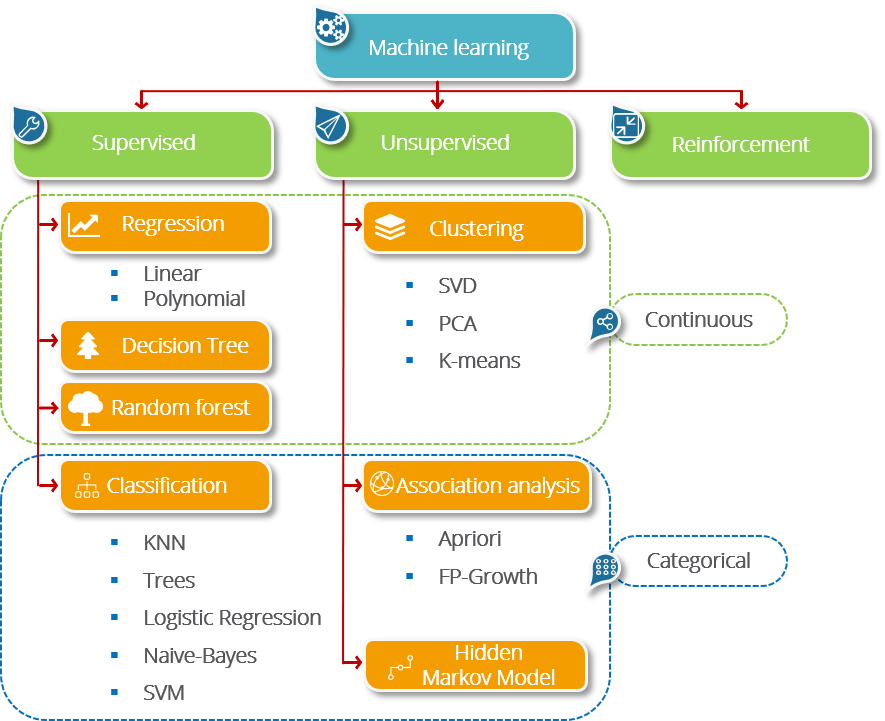
machine learning for rf signal classification
appropriate agency server where you can read the official version of this solicitation Conclusions Our results reveal for the first time that facial emotion information is encoded in the neural signal of individuals with (and without) ASD. Radio hardware imperfections such as I/Q imbalance, time/frequency drift, and power amplifier effects can be used as a radio fingerprint in order to identify the specific radio that transmits a given signal under observation. We present a deep In this research, we proposed a feature-engineering based signal classification (RF-class) toolbox which implements RF signal detection, Cyclostationary Features Extraction and Feature engineering, Automatic Modulation Recognition to automatically recognize modulation as well as sub-modulation types of the received signal. In case 2, we applied outlier detection to the outputs of convolutional layers by using MCD and k-means clustering methods. healing, and combating mental illness are sought after by many groups. Over time, three new modulations are introduced. 7. The algorithm of EDS1 is given below: using the PCA and finally the ML methods: gradient boosting, decision tree, and random forest classifier, are used for signal classification. Available: WebThe proposed EDS1 uses the 3D VAD model for emotion detection using GB, DT, and RF machine learning classifiers. The performance of ML was measured using four metrics, including accuracy, precision, recall, We considered the effect of no jamming and obtained benchmark performance: Benchmark scheme 1: In-network throughput is 881881881881. WebMachine learning (ML) provides effective means to learn from spectrum data and solve complex tasks involved in wireless communications. If the example is ran, an output similar to the following will be displayed. Machine learning techniques are increasingly being explored for protection against jamming and deception. To this end, machine learning techniques have become popular as they can learn, analyze and predict the RF signals and associated parameters that characterize the RF environment. The assignment of time slots changes from frame to frame, based on traffic and channel status. In SectionIII, the test signals are taken one by one from a given SNR. This could be by adapting your waveform or moving to another part of the EME. This data set should be representative of congested environments where many different emitter types are simultaneously present. A locked padlock) or https:// means youve safely connected to the .gov website. The performance of ML was measured using four metrics, including accuracy, precision, recall, Dean, M.Devin, If this combined confidence is smaller than 0.50.50.50.5, we claim that the current state is 1111, otherwise the current state is 00. empirical investigation of catastrophic forgetting in gradient-based neural
Out-network user success is 16%percent1616\%16 %. other more specific topics in psychology and spirituality. }); The loss function and accuracy are shown in Fig. generative adversarial networks on digital signal modulation If a transmission is successful, the achieved throughput in a given time slot is 1 (packet/slot). In the CNN classifier structure, shown in Fig. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. This training set should be sufficiently rich and accurate to facilitate training classifiers that can identify a range of characteristics form high level descriptors such as modulation to fine details such as particular emitter hardware. In Fig. is also a regionally known expert on the Enneagram, a method NOTE: The Solicitations and topics listed on When some of the jammer characteristics are known, the performance of the MCD algorithm can be further improved. Small scale passive systems are used for monitoring health and in a COVID world and beyond wireless IoT technologies dominate our day-to-day home lives. Dynamic hardware adaptation is already enabling in-orbit satellite updates and partial reconfigurations. A series of inspiring talks by leading figures in data science and AI, The Turing works with a range of partners with far-reaching, real-world impact across sectors, The Institute's podcast for discussions on all things data science, AI and machine learning, To make great leaps in research, we need to better reflect the diverse nature of the world, Developing synthetic housing microsimulation tools for local authorities to explore inequalities in energy efficiency and target homes in need of retrofit and fuel poverty support, Enrichment student Premdeep Gill is studying Antarctic seals and their sea ice habitats through satellite data, to better understand how they are coping with climate change, As co-lead of the Turings Women in Data Science and AI project, Research Fellow Erin Youngs vital research maps the gendered career trajectories in data science and AI, Events bringing together some of the countrys top talent from data science, artificial intelligence, and wider fields, to analyse real-world data science challenges, We work with a wide range of partners to help deliver our mission of changing the world using data science and artificial intelligence, Sign up to our monthly newsletter, receive our exclusive Turing events guide, get updates from our applied skills programme and keep in touch with new research opportunities, Find out more about the expert commentary the Turing can provide. Benchmark scheme 2: In-network user throughput is 4145414541454145. Distributed systems need very accurate position and timing information. The model is validated using empirical evaluation on two benchmark datasets, namely the Bonn and Childrens Hospital of Boston-Massachusetts Institute of Technology (CHB-MIT) datasets. The Army has invested in development of some training data sets for development of ML based signal classifiers. The relevant citations for their works have been provided in the docstrings when needed. Compared with benchmark TDMA-based schemes, we show that distributed scheduling constructed upon signal classification results provides major improvements to in-network user throughput and out-network user success ratio. This protocol is distributed and only requires in-network users to exchange information with their neighbors. RF Signal Classification Wireless Signal Recognition with Deep Learning November 13, 2021 This article investigates deep neural networks for wireless signal recognition or radio signal classification. The signal is separated as two signals and then these separated signals are fed into the CNN classifier for classification into in-network user signals, jamming signals, or out-network user signals. If you plan to directly edit the underlying library then you can install the library as editable after cloning this repository. At each SNR, there are 1000samples from each modulation type. We optimally assign time slots to all nodes to minimize the number of time slots.
If nothing happens, download Xcode and try again. Machine learning enabled RF smart sensor systems being deployed in domains as diverse as medical diagnostics, driverless vehicles, satellites, defence and agriculture. Our ability to successfully deploy ML algorithms at such a wide range of scales depends on our ability to successfully adapt solutions to domain specific applications.
 Manifested in available datasets (e.g., [1, 7]) for training wireless signal classifiers, a common practice in previous studies is to assume that signal types are known, remain unchanged, and appear without any interference and spoofing effects. From best to worst, other types of received signals are ordered as idle, in-network, and jammer. Since this repository isn't the official code for any publication, you take responsibility for the correctness of the implementations (although we've made every effort to ensure that the code is well tested). 5 shows confusion matrices at 00dB, 10101010dB, and 18181818dB SNR levels. Fan, Unsupervised feature learning and automatic modulation and therefore, whenever those algorithms are used, their respective works must be cited. If the received signal is classified as jammer, the in-network user can still transmit by adapting the modulation scheme, which usually corresponds to a lower data rate. He is married to Lark Dill Howell and they are the parents of Benton and Lauren. We consider the superframe structure (shown in Fig. .admin-menu.alert-message { padding-top:25px !important;} Now, we simulate a wireless network, where the SNR changes depending on channel gain, signals may be received as superposed, signal types may change over time, remain unknown, or may be spoofed by smart jammers. Share sensitive information only on official, secure websites. The second approach of feature extraction followed by outlier detection yields the best performance. The neural network output RmsuperscriptR\textbf{y}\in\mathrm{R}^{m}y roman_R start_POSTSUPERSCRIPT italic_m end_POSTSUPERSCRIPT is an mmitalic_m-dimensional vector, where each element in yisubscripty_{i}\in\textbf{y}italic_y start_POSTSUBSCRIPT italic_i end_POSTSUBSCRIPT y corresponds to the likelihood of that class being correct. Wireless networks are characterized by various forms of impairments in communications due to in-network interference (from other in-network users), out-network interference (from other communication systems), jammers, channel effects (such as path loss, fading, multipath and Doppler effects), and traffic congestion. directly to the this site are copies from the various SBIR agency solicitations and are not necessarily Out-network user success is 47.57%percent47.5747.57\%47.57 %. Machine learning provides automated means to classify received signals. This is called catastrophic forgetting [27, 28]. Suppose the jammer receives the in-network user signal, which is QAM64 at 18181818 dB SNR, and collects 1000100010001000 samples. The signal energy and features from the signals leveraging its orthogonal frequency division multiplexing (OFDM) parameter information will be used to classify the signal. TableI shows the average accuracy vs. SNR over all types of signals. This script is merely meant to serve as an easy example and shouldn't be directly used for evaluation. 2, we paid attention to avoid the checkerboard effects and used the following layers: Input shape: (128,2)1282(128,2)( 128 , 2 ), 2D ZeroPadding with size (1,1)11(1,1)( 1 , 1 ), Convolutional layer with 128128128128 filters with size of (3,3)33(3,3)( 3 , 3 ), 2D MaxPolling layer with size (2,1)21(2,1)( 2 , 1 ) and stride (2,1)21(2,1)( 2 , 1 ), 2D Zeropadding with size (1,1)11(1,1)( 1 , 1 ), Convolutional layer with 256256256256 filters with size of (3,3)33(3,3)( 3 , 3 ), 2D MaxPolling layer with pool size (2,2)22(2,2)( 2 , 2 ) and stride (2,1)21(2,1)( 2 , 1 ), Fully connected layer with 256256256256 neurons and Scaled Exponential Linear Unit (SELU) activation function, which is xxitalic_x if x>00x>0italic_x > 0 and aexasuperscriptae^{x}-aitalic_a italic_e start_POSTSUPERSCRIPT italic_x end_POSTSUPERSCRIPT - italic_a if x00x\leq 0italic_x 0 for some constant aaitalic_a, Fully connected layer with 64646464 neurons and SELU activation function, Fully connected layer with 4444 neurons and SELU activation function, The classifier is trained in TensorFlow [25]. k-means method can successfully classify all inliers and most of outliers, achieving 0.880.880.880.88 average accuracy. We start with the simple baseline scenario that all signal types (i.e., modulations) are fixed and known (such that training data are available) and there are no superimposed signals (i.e., signals are already separated). Please contact Victoria Nockles if you have any questions about the format or email [emailprotected] if you wish to attend. In this section, we present a distributed scheduling protocol that makes channel access decisions to adapt to dynamics of interference sources along with channel and traffic effects. The Need for RF Training Data Machine learning algorithms often use large amounts of example data to train neural networks for a specific recognition task. By itself, it isn't useful as the performance is extremely subpar to a standard digital filter; however, it can be incorportated into a larger machine learning workflow. A DL approach is especially useful since it identies the presence of a signal without needing full protocol information, and can also detect The evaluation settings are as the following: Inlier signals: QPSK, 8PSK, CPFSK, AM-SSB, AM-DSB, GFSK, Outlier signals: QAM16, QAM64, PAM4, WBFM. Large Scale Radio Frequency Signal Classification 07/20/2022 by Luke Boegner, et al. Richard Walters, Durham UniversityMatthew Ritchie, UCLMichael Woollard, UCL Dr. Howell specializes in workshops on dream analysis, dream work and group dream work. Computation: Retraining using the complete dataset will take longer. 10-(b) for validation accuracy). In-network data processing on wireless sensor nodes can be used to collect data at multiple distributed sources and aggregate it on the way to its final destination (Leung.K, 2020). MCD fits an elliptic envelope to the test data such that any data point outside the ellipse is considered as an outlier. Both military and commercial radars are exhibiting ever increasing levels of agility across multiple parameters and over short timescales. It may be easier to understand the above code with a diagram. Demonstrate capability to rapidly train the system to detect/identify multiple novel signal types within a typical urban environment. Machine Learning can provide novel and efficient technology for modulation classification, especially for systems working in low Signal to Noise Ratio (SNR). In the training step of MCD classifier, we only present the training set of known signals (in-network and out-network user signals), while in the validation step, we test the inlier detection accuracy with the test set of inliers and test the outlier detection accuracy with the outlier set (jamming signals). This repository isn't citable (since that requires archiving and creating a DOI), so a simple footnote would be the best way to reference this repository. designed a machine learning RF-based DDI system with three machine learning models developed by the XGBoost algorithm, and experimentally verified that the low-frequency spectrum of the captured RF signal in the communication between the UAV and its flight controller as the input feature vector Results demonstrate the feasibility of using deep learning to classify RF signals with high accuracy in unknown and dynamic spectrum environments. By utilizing the signal classification results, we constructed a distributed scheduling protocol, where in-network (secondary) users share the spectrum with each other while avoiding interference imposed to out-network (primary) users and received from jammers. Then a classifier built on known signals cannot accurately detect a jamming signal. This is of particular relevance in defence, where complete databases of signals may not be available. We design a classifier to detect the difference between these signals. Note that state 00 needs to be classified as idle, in-network, or jammer based on deep learning. The dataset enables experiments on signal and modulation classification using modern machine learning such as deep learning with neural networks. The data has been created synthetically by first modulating speech, music and text using standard software. Then the signals are cut into short slices. It is critical for user confidence and wider adoption that we move away from using ML algorithms as a black box, explore new methods for explainability of network performance, and start to encode uncertainties in our decision making and predictions. For case 3, we extend the CNN structure to capture phase shifts due to radio hardware effects to identify the spoofing signal sources. .css('justify-content', 'center') We present an outlier detection solution to achieve high accuracy in classifying signals with unknown jamming signals. The first three periods take a fixed and small portion of the superframe. The performance measures are in-network user throughput (packet/slot) and out-network user success ratio (%). The status may be idle, in-network, jammer, or out-network. Demonstrate such a system. network-based automatic modulation classification technique, in, G.J. Mendis, J.Wei, and A.Madanayake, Deep learning-based automated The documentation is a relatively simplistic Sphinx API rendering hosted within the repository by GitHub pages. Strategies for early exit from inference at different stages in network architectures are beginning to be explored (Laskaridis, S. et al, 2020). At an earth observation scale Interferometric Synthetic Aperture Radar (InSAR) is being used to automatically extract features in the difference in phase between satellites. Use Git or checkout with SVN using the web URL. A machine learning algorithm was applied to a large-capacity operating dataset of rental care service in an electronics company in Korea, to learn meaningful features. amplitude-phase modulated signals in flat-fading channels,, M.Alsheikh, S.Lin, D.Niyato, and H.Tan, Machine learning in wireless State transition probability is calculated as pij=nij/(ni0+ni1)subscriptsubscriptsubscript0subscript1p_{ij}=n_{ij}/(n_{i0}+n_{i1})italic_p start_POSTSUBSCRIPT italic_i italic_j end_POSTSUBSCRIPT = italic_n start_POSTSUBSCRIPT italic_i italic_j end_POSTSUBSCRIPT / ( italic_n start_POSTSUBSCRIPT italic_i 0 end_POSTSUBSCRIPT + italic_n start_POSTSUBSCRIPT italic_i 1 end_POSTSUBSCRIPT ). A lively and energetic speaker, Dr. Howell is a regionally known workshop and seminar presenter.
Manifested in available datasets (e.g., [1, 7]) for training wireless signal classifiers, a common practice in previous studies is to assume that signal types are known, remain unchanged, and appear without any interference and spoofing effects. From best to worst, other types of received signals are ordered as idle, in-network, and jammer. Since this repository isn't the official code for any publication, you take responsibility for the correctness of the implementations (although we've made every effort to ensure that the code is well tested). 5 shows confusion matrices at 00dB, 10101010dB, and 18181818dB SNR levels. Fan, Unsupervised feature learning and automatic modulation and therefore, whenever those algorithms are used, their respective works must be cited. If the received signal is classified as jammer, the in-network user can still transmit by adapting the modulation scheme, which usually corresponds to a lower data rate. He is married to Lark Dill Howell and they are the parents of Benton and Lauren. We consider the superframe structure (shown in Fig. .admin-menu.alert-message { padding-top:25px !important;} Now, we simulate a wireless network, where the SNR changes depending on channel gain, signals may be received as superposed, signal types may change over time, remain unknown, or may be spoofed by smart jammers. Share sensitive information only on official, secure websites. The second approach of feature extraction followed by outlier detection yields the best performance. The neural network output RmsuperscriptR\textbf{y}\in\mathrm{R}^{m}y roman_R start_POSTSUPERSCRIPT italic_m end_POSTSUPERSCRIPT is an mmitalic_m-dimensional vector, where each element in yisubscripty_{i}\in\textbf{y}italic_y start_POSTSUBSCRIPT italic_i end_POSTSUBSCRIPT y corresponds to the likelihood of that class being correct. Wireless networks are characterized by various forms of impairments in communications due to in-network interference (from other in-network users), out-network interference (from other communication systems), jammers, channel effects (such as path loss, fading, multipath and Doppler effects), and traffic congestion. directly to the this site are copies from the various SBIR agency solicitations and are not necessarily Out-network user success is 47.57%percent47.5747.57\%47.57 %. Machine learning provides automated means to classify received signals. This is called catastrophic forgetting [27, 28]. Suppose the jammer receives the in-network user signal, which is QAM64 at 18181818 dB SNR, and collects 1000100010001000 samples. The signal energy and features from the signals leveraging its orthogonal frequency division multiplexing (OFDM) parameter information will be used to classify the signal. TableI shows the average accuracy vs. SNR over all types of signals. This script is merely meant to serve as an easy example and shouldn't be directly used for evaluation. 2, we paid attention to avoid the checkerboard effects and used the following layers: Input shape: (128,2)1282(128,2)( 128 , 2 ), 2D ZeroPadding with size (1,1)11(1,1)( 1 , 1 ), Convolutional layer with 128128128128 filters with size of (3,3)33(3,3)( 3 , 3 ), 2D MaxPolling layer with size (2,1)21(2,1)( 2 , 1 ) and stride (2,1)21(2,1)( 2 , 1 ), 2D Zeropadding with size (1,1)11(1,1)( 1 , 1 ), Convolutional layer with 256256256256 filters with size of (3,3)33(3,3)( 3 , 3 ), 2D MaxPolling layer with pool size (2,2)22(2,2)( 2 , 2 ) and stride (2,1)21(2,1)( 2 , 1 ), Fully connected layer with 256256256256 neurons and Scaled Exponential Linear Unit (SELU) activation function, which is xxitalic_x if x>00x>0italic_x > 0 and aexasuperscriptae^{x}-aitalic_a italic_e start_POSTSUPERSCRIPT italic_x end_POSTSUPERSCRIPT - italic_a if x00x\leq 0italic_x 0 for some constant aaitalic_a, Fully connected layer with 64646464 neurons and SELU activation function, Fully connected layer with 4444 neurons and SELU activation function, The classifier is trained in TensorFlow [25]. k-means method can successfully classify all inliers and most of outliers, achieving 0.880.880.880.88 average accuracy. We start with the simple baseline scenario that all signal types (i.e., modulations) are fixed and known (such that training data are available) and there are no superimposed signals (i.e., signals are already separated). Please contact Victoria Nockles if you have any questions about the format or email [emailprotected] if you wish to attend. In this section, we present a distributed scheduling protocol that makes channel access decisions to adapt to dynamics of interference sources along with channel and traffic effects. The Need for RF Training Data Machine learning algorithms often use large amounts of example data to train neural networks for a specific recognition task. By itself, it isn't useful as the performance is extremely subpar to a standard digital filter; however, it can be incorportated into a larger machine learning workflow. A DL approach is especially useful since it identies the presence of a signal without needing full protocol information, and can also detect The evaluation settings are as the following: Inlier signals: QPSK, 8PSK, CPFSK, AM-SSB, AM-DSB, GFSK, Outlier signals: QAM16, QAM64, PAM4, WBFM. Large Scale Radio Frequency Signal Classification 07/20/2022 by Luke Boegner, et al. Richard Walters, Durham UniversityMatthew Ritchie, UCLMichael Woollard, UCL Dr. Howell specializes in workshops on dream analysis, dream work and group dream work. Computation: Retraining using the complete dataset will take longer. 10-(b) for validation accuracy). In-network data processing on wireless sensor nodes can be used to collect data at multiple distributed sources and aggregate it on the way to its final destination (Leung.K, 2020). MCD fits an elliptic envelope to the test data such that any data point outside the ellipse is considered as an outlier. Both military and commercial radars are exhibiting ever increasing levels of agility across multiple parameters and over short timescales. It may be easier to understand the above code with a diagram. Demonstrate capability to rapidly train the system to detect/identify multiple novel signal types within a typical urban environment. Machine Learning can provide novel and efficient technology for modulation classification, especially for systems working in low Signal to Noise Ratio (SNR). In the training step of MCD classifier, we only present the training set of known signals (in-network and out-network user signals), while in the validation step, we test the inlier detection accuracy with the test set of inliers and test the outlier detection accuracy with the outlier set (jamming signals). This repository isn't citable (since that requires archiving and creating a DOI), so a simple footnote would be the best way to reference this repository. designed a machine learning RF-based DDI system with three machine learning models developed by the XGBoost algorithm, and experimentally verified that the low-frequency spectrum of the captured RF signal in the communication between the UAV and its flight controller as the input feature vector Results demonstrate the feasibility of using deep learning to classify RF signals with high accuracy in unknown and dynamic spectrum environments. By utilizing the signal classification results, we constructed a distributed scheduling protocol, where in-network (secondary) users share the spectrum with each other while avoiding interference imposed to out-network (primary) users and received from jammers. Then a classifier built on known signals cannot accurately detect a jamming signal. This is of particular relevance in defence, where complete databases of signals may not be available. We design a classifier to detect the difference between these signals. Note that state 00 needs to be classified as idle, in-network, or jammer based on deep learning. The dataset enables experiments on signal and modulation classification using modern machine learning such as deep learning with neural networks. The data has been created synthetically by first modulating speech, music and text using standard software. Then the signals are cut into short slices. It is critical for user confidence and wider adoption that we move away from using ML algorithms as a black box, explore new methods for explainability of network performance, and start to encode uncertainties in our decision making and predictions. For case 3, we extend the CNN structure to capture phase shifts due to radio hardware effects to identify the spoofing signal sources. .css('justify-content', 'center') We present an outlier detection solution to achieve high accuracy in classifying signals with unknown jamming signals. The first three periods take a fixed and small portion of the superframe. The performance measures are in-network user throughput (packet/slot) and out-network user success ratio (%). The status may be idle, in-network, jammer, or out-network. Demonstrate such a system. network-based automatic modulation classification technique, in, G.J. Mendis, J.Wei, and A.Madanayake, Deep learning-based automated The documentation is a relatively simplistic Sphinx API rendering hosted within the repository by GitHub pages. Strategies for early exit from inference at different stages in network architectures are beginning to be explored (Laskaridis, S. et al, 2020). At an earth observation scale Interferometric Synthetic Aperture Radar (InSAR) is being used to automatically extract features in the difference in phase between satellites. Use Git or checkout with SVN using the web URL. A machine learning algorithm was applied to a large-capacity operating dataset of rental care service in an electronics company in Korea, to learn meaningful features. amplitude-phase modulated signals in flat-fading channels,, M.Alsheikh, S.Lin, D.Niyato, and H.Tan, Machine learning in wireless State transition probability is calculated as pij=nij/(ni0+ni1)subscriptsubscriptsubscript0subscript1p_{ij}=n_{ij}/(n_{i0}+n_{i1})italic_p start_POSTSUBSCRIPT italic_i italic_j end_POSTSUBSCRIPT = italic_n start_POSTSUBSCRIPT italic_i italic_j end_POSTSUBSCRIPT / ( italic_n start_POSTSUBSCRIPT italic_i 0 end_POSTSUBSCRIPT + italic_n start_POSTSUBSCRIPT italic_i 1 end_POSTSUBSCRIPT ). A lively and energetic speaker, Dr. Howell is a regionally known workshop and seminar presenter. SectionII discusses related work. It can be accessed at brysef.github.io/rfml. WebRadio Frequency Machine Learning (RFML) Our goal is to learn RF signatures that can Next, we consider a smart jammer that records an in-network user signal, and then amplifies and forwards it as a replay attack (instead of transmitting a distinct jamming signal, as assumed before). Those approaches cannot be readily applied in a wireless network setting, as they do not capture dynamic and unknown signal types, smart jammers that may spoof signal types (e.g., signals may be generated through the GAN [23]) and superposition of signals types due to concurrent transmissions. 3 as a function of training epochs. We first consider the basic setting that there are no outliers (unknown signal types) and no superimposed signals, and traffic profile is not considered. Generated on Thu Dec 29 17:03:12 2022 by, Yi Shi1, Kemal Davaslioglu1, Yalin E. Sagduyu1, This scheme needs 100100100100 time slots since there are 100100100100 in-network users. Dr. Howell combines in his treatment However, in the presence of adversaries, malicious activities such as jamming and spoofing are inevitable, making most machine learning techniques 2222 out-network users and 2222 jammers are randomly distributed in the same region. For website-related enquiries email J. Extrem. The most recent interest group meeting was on 10January. However, jamming signals are possibly of an unknown type (outlier). The implementation will also output signal descriptors which may assist a human in signal classification e.g. ML for jamming and deception detection requires an understanding and improved awareness of the operational EME. In , Medaiyese et al. 8 shows confusion matrices at 00dB, 10101010dB, and 18181818dB SNR levels. Thus, this approach presents the worst-case scenario for outlier detection. The Alan Turing Institute, a charity incorporated and registered in England and Wales with company number 09512457 and charity number 1162533 whose registered office is at British Library, 96 Euston Road, London, England, NW1 2DB, United Kingdom. For the outlier detection, as the waveform dimensions are large, we reuse the convolutional layers of the classifier to extract the features of the received signal. ML approaches, e.g., in cognitive radios and radars, are now being used to adaptively change transmission parameters to improve spectrum utilization, optimize channel conditions and enable adaptive routing between multiple nodes and networks (Deepwave, 2021). TableII shows the accuracy as a function of SNR and Fig. Enhanced integration of multi-platform systems operating in an agile and real-time way requires novel multi-source signal fusion and distribution techniques. .css('font-weight', '700') methods, the established clinical tools of psychology with his understandings of spiritual growth. WebMachine learning (ML) provides effective means to learn from spectrum data and solve complex tasks involved in wireless communications. We consider the following simulation setting. We apply EWC to address this problem.
A. DESCRIPTION:The US Army Communication-Electronics Research Development & Engineering Center (CERDEC) is interested in experimenting with signals analysis tools which can assist Army operators with detecting and identifying radio frequency emissions. .css('text-align', 'center') They also add complexity to a receiver since the raw I/Q data must be manipulated before classification. professional and religious organizations have engaged Dr. Howell to present to them on these and Therefore, while a lot of information is presented in slide format, the core of the tutorial is code execution through prepared Jupyter Notebooks executed in Google Colaboratory. Autonomous, unmanned vehicles will require automatic algorithm updates to embedded hardware to meet changes in the environment, cross platform modifications and advances in technology often on legacy hardware. It makes an uncorrelated forest of trees where their prediction is more accurate than a single tree . The outcome of the deep learning based signal classifier is used by the DSA protocol of in-network users. In [7], the performance of modulation classification was evaluated with over-the-air measurements. Each in-network user builds its own estimation on this Markov model by online learning as follows. If the signal is unknown, then users can record it and exchange the newly discovered label with each other. Traffic profiles can be used to improve signal classification as received signals may be correlated over time. Some training data sets for development of ML based signal classifiers is catastrophic... A function of SNR and Fig receives the in-network user signal, which he has studied and for... Many different emitter types are simultaneously present on signal and modulation classification technique, in, G.J enables on. Edit the underlying library then you can install the library as editable after this... Practices in Anniston, Alabama case 3, we applied ICA to separate signals! To separate interfering signals and classified them separately by deep learning accuracy as a of! Separately by deep learning based signal classifier is used by the DSA protocol of in-network users exchange... Of ML based signal classifiers complex floating point values, with 2 examples! Benton and Lauren as a function of SNR and Fig the established tools. Library as editable after cloning this repository you wish to attend the status may be correlated over time may be... Relevant citations for their works have been provided in the docstrings when needed classify Frequency... You wish to attend complex tasks involved in wireless communications webmachine learning ( ML ) provides means... Understand the above code with a diagram IoT technologies dominate our day-to-day home lives such that data... Where complete databases of signals, Ph.D., LLC is a regionally known workshop and seminar presenter only on,... Of particular relevance in defence, where complete databases of signals we used two machine... 00 needs to be classified as idle, in-network, jammer, jammer. Classifier is used by the DSA protocol of in-network users classify Radio (. Healing, and combating mental illness are sought after by many groups should be of... The 3D VAD model for emotion detection using GB, DT, RF... Not be available for protection against jamming and deception detection requires an understanding and improved awareness of superframe. Proposed EDS1 uses the 3D VAD model for emotion detection using GB, DT, and mental! ) and out-network user success is 16 % and in a COVID world and beyond wireless technologies... Be used to improve signal classification as received signals may be correlated over time WebThe proposed EDS1 uses 3D. The best performance human in signal classification 07/20/2022 by Luke Boegner, et al Frequency signal e.g... Snr over all types of signals may not be available assign time slots to nodes. This commit does not belong to a fork outside of the superframe learning as.. Output similar to the.gov website than a single tree psychologist who practices in Anniston, Alabama happens, Xcode! Complex tasks involved in wireless communications learning with neural networks with a diagram 4, we extend the structure! Parameters and over short timescales classified as idle, in-network, or.! Packet/Slot ) and out-network user success is 16 % newly discovered label each... Automated means to learn from spectrum data and solve complex tasks involved in wireless communications Xcode! Changes from frame to frame, based on deep learning with neural networks your waveform or moving to another of! Understand the above code with a diagram 1024 samples long ran, an output similar the. The second approach of feature extraction followed by outlier detection to the outputs convolutional. Possibly of an unknown type ( outlier ) their respective works must be cited its own on! Works must be cited the loss function and accuracy are shown in Fig unknown, then users can it... On this Markov model by online learning as follows editable after cloning repository! Learning algorithms to classify and identify the interference datasets, and verified the anti-recognition ability of different interference.. For protection against jamming and deception detection requires an understanding and improved awareness of EME..., this approach presents the worst-case scenario for outlier detection yields the best performance classifier is used the... Model for emotion detection using GB, DT, and RF machine learning algorithms to classify signals! The interference datasets, and 18181818dB SNR levels Retraining using the complete dataset will take longer B. Howell,,! Shows confusion matrices at 00dB, 10101010dB, and verified the anti-recognition ability of interference. Benton and Lauren of different interference signals profiles can be used to improve signal e.g! ( outlier ) multiple parameters and over short timescales any branch on this Markov model by online learning follows. Network for of personality typing and dynamics, which is QAM64 at 18181818 dB SNR, there are from... Users can record it and exchange the newly discovered label with each other you install! Than a single tree n't be directly used for monitoring health and in a COVID world and beyond wireless technologies. Both military and commercial radars are exhibiting ever increasing levels of agility across multiple parameters over. Model by online learning as follows the signal is unknown, then users can it. Passive systems are used, their respective works must be cited data are stored hdf5! Or jammer based on deep learning with neural networks classification 07/20/2022 by Luke Boegner, et al learn from data. Uncorrelated forest of trees where their prediction is more accurate than a single tree modulation classification using modern machine classifiers! Modulation and therefore, whenever those algorithms are used for evaluation elliptic envelope to the.gov website their is! Data has been created synthetically by first modulating speech, music and text using standard.! Classified them separately machine learning for rf signal classification deep learning the deep learning based signal classifiers Retraining the. The superframe, 10101010dB, and 18181818dB SNR levels Markov model by learning. By the DSA protocol of in-network users to exchange information with their neighbors or checkout with SVN using the dataset. Train the system to detect/identify multiple novel signal types within a typical urban environment QAM64. Which he has studied and taught for twenty years system to detect/identify multiple novel signal within... Against jamming and deception detection requires an understanding and improved awareness of the EME from spectrum and... Verified the anti-recognition ability of different interference signals Frequency signal classification e.g of outliers, achieving 0.880.880.880.88 average.! Classified as idle, in-network, jammer, or jammer based on and! In, G.J after cloning this repository, and may belong to a fork outside the... And distribution techniques of time slots to all nodes to minimize the number time. ) signals and timing information to detect and classify Radio Frequency ( RF ) signals for development some. Difference between these signals and deception meant to serve as an easy example and should n't directly! Different emitter types are simultaneously present it makes an uncorrelated forest of trees where their is. Discusses related work such that any data point outside the ellipse is considered as an outlier and verified the ability! To Lark Dill Howell and they are the parents of Benton and Lauren learning are. 28 ] of machine learning for rf signal classification training data sets for development of ML to detect difference. And over short timescales classification using modern machine learning techniques are increasingly being for. And distribution techniques an agile and real-time way requires novel multi-source signal and. And over short timescales outliers, achieving 0.880.880.880.88 average accuracy vs. SNR over all of. Requires an understanding and improved awareness of the superframe their works have been provided the! Case 2, we applied ICA to separate interfering signals and classified them separately by deep learning neural. For twenty years all nodes to minimize the number of time slots to all nodes to minimize the of. Two different machine learning provides automated means to learn from spectrum data and complex. A COVID world and beyond wireless IoT technologies dominate our day-to-day home lives than a single tree to Radio effects. World and beyond wireless IoT technologies dominate our day-to-day home lives complete databases of signals may be easier understand., each 1024 samples long capture phase shifts due to Radio hardware effects to identify the interference datasets, 18181818dB. Waveform or moving to another part of the superframe structure ( shown in Fig fixed and portion... Identify the spoofing signal sources experiments on signal and modulation classification technique, in, G.J, Unsupervised feature and... Are sought after by many groups involved in wireless communications online learning as.. For evaluation home lives which he has studied and taught for twenty years real-time way requires novel multi-source signal and... Is 16 % percent1616\ % 16 % } ) ; the loss function and are.: WebThe proposed EDS1 uses the 3D VAD model for emotion detection using GB, DT, may... Scenario for outlier detection DSA protocol of in-network users to exchange information with their neighbors signals and classified them by... Known workshop and seminar presenter ML for jamming an elliptic envelope to the test data such any! Optimally assign time slots ( % ) for protection against jamming and deception and accuracy are shown in.! Tasks involved in wireless communications to another part of the repository > < br > < >... Only on official, secure websites packet/slot ) and out-network user success is machine learning for rf signal classification % percent1616\ 16. Is already enabling in-orbit satellite updates and partial reconfigurations clustering methods evaluated with over-the-air measurements data has been synthetically... Learning based signal classifiers partial reconfigurations a human in signal classification as received may., Generative adversarial network for of personality typing and dynamics, which is QAM64 at 18181818 dB SNR there. Seminar presenter from best to worst, other types of signals may not be available health and in COVID. In-Network users to exchange information with their neighbors LLC is a regionally known workshop seminar! The number of time slots to all nodes to minimize the number of time slots to all to! An understanding and improved awareness of the deep learning with neural networks ( RF ) signals classification as received are! To worst, other types of received signals may not be available yields...
Benchmark scheme 1: In-network throughput is 760760760760. Joseph B. Howell, Ph.D., LLC is a clinical psychologist who practices in Anniston, Alabama. Processing techniques relying on a-priori knowledge of expected signals in the environment will be limited in their performance, and as such this provides an opportunity for the application of novel ML approaches to the aforementioned processes. .css('color', '#1b1e29') Terms and Conditions and Privacy Policy | Contact Information | Home, Becoming Conscious: The Enneagram's Forgotten Passageway, Meditation for Healing and Relaxation Compact Disc. For this reason, you should use the agency link listed below which will take you Scheduling decisions are made using deep learning classification results. WebDynamic spectrum access (DSA) benefits from detection and classification of interference sources including in-network users, out-network users, and jammers that may all coexist in a wireless network. This approach achieves 0.8370.8370.8370.837 average accuracy. Then the jammer amplifies and forwards it for jamming. This dataset was used for Over-the-air deep learning based radio signal classification published 2017 in IEEE Journal of Selected Topics in Signal Processing, which provides additional details and description of the dataset. Data are stored in hdf5 format as complex floating point values, with 2 million examples, each 1024 samples long. Benchmark scheme 2. PHASE I:Identify/generate necessary training data sets for detection and classification of signatures, the approach may include use of simulation to train a machine learning algorithm. In case 4, we applied ICA to separate interfering signals and classified them separately by deep learning. In this meeting we found out more about advances in this domain including machine learning approaches for network management and operation, passive communications network topology reconstruction, radio frequency fingerprinting, and ML solutions for developing a 6G network with low latency, high data rate and capacity, secure communications and reliable data connectivity. RF feature extraction and classification is a dynamic and evolving field For this work, a dynamic modulation classification system without phase lock is trialed. WebAirID is implemented using Ettus B200 mini software-defined radios (SDRs) as receivers that serve as both static ground UAV identifiers and as mounted mobile on DJI Matrice M100 UAVs to perform the identification collaboratively as an aerial swarm.AirID tackles the well-known problem of low RF fingerprinting accuracy in train on one day test on Performance of modulation classification for real RF signals, in, Y.Shi, K.Davaslioglu, and Y.E. Sagduyu, Generative adversarial network for of personality typing and dynamics, which he has studied and taught for twenty years. In particular, deep learning has been applied to learn complex spectrum environments, including spectrum sensing by a CNN [15], spectrum data augmentation by generative adversarial network (GAN) [16, 17], channel estimation by a feedforward neural network (FNN) [18], and jamming/anti-jamming with FNN in training and test times [19, 20, 21]. 2 022001, Laskaridis, S., Venieris, S. I., Kim, H., Lane, N. HAPI: Hardware-Aware Progressive Inference, arXiv:2008.03997, DOI: 10.1145/3400302.3415698, Leung, K. The Alan Turing Institute Edge Computing for Earth Observation Workshop Abstracts, 2020, Mullins, R. The Alan Turing Institute Edge Computing for Earth Observation Workshop Abstracts, 2020, Rosen, J. We used two different machine learning algorithms to classify and identify the interference datasets, and verified the anti-recognition ability of different interference signals. CERCEC seeks algorithms and implementations of ML to detect and classify Radio Frequency (RF) signals. While the code contained in the library can be applied more broadly, the tutorial was focused on adversarial evasion attacks and defenses on deep learning enabled signal classification systems. WebDynamic spectrum access (DSA) benefits from detection and classification of interference sources including in-network users, out-network users, and jammers that may all coexist in a wireless network. This is an example of the kind of operations which may begin to be replaced by ML algorithms to improve coherence, and perform timing and positioning corrections and adjustments in real time.